A new scam uses Netflix to steal personal information from users across Latin America. Through an email that offers a three-month trial subscription to the streaming service, hackers have access to your information and data from Hotmail and Hot maill accounts .
Netflix wants global catalog and end of content block by country
 New deal uses Netflix to steal personal data (Photo: Divulga / Netflix)
New deal uses Netflix to steal personal data (Photo: Divulga / Netflix)
The basic idea is that scammers use an application previously configured by the user to access a program or service and then implement an OAuth APLI through a token. In this way, they can access the victim's information even when the user is not logged in to their account.
According to Roberto Martinez, security analyst at Kaspersky Lab, "This type of attack is very peculiar because it does not involve stealing usernames or passwords, nor is it a cryptographic attack." Further, it says that in this case, "the threat is known as an Open Redirect attack group".
know more
How it works
The process basically follows three steps. First, the victim receives an email offering three months of free subscription to Netflix . When you click the link, you are redirected to the provider's site that you want to authenticate to, Hotmail, or Outlook.com Then enter your credentials and a screen appears asking for access clearance.
Is Netflix worth it? Comment on the TechTudo Forum.
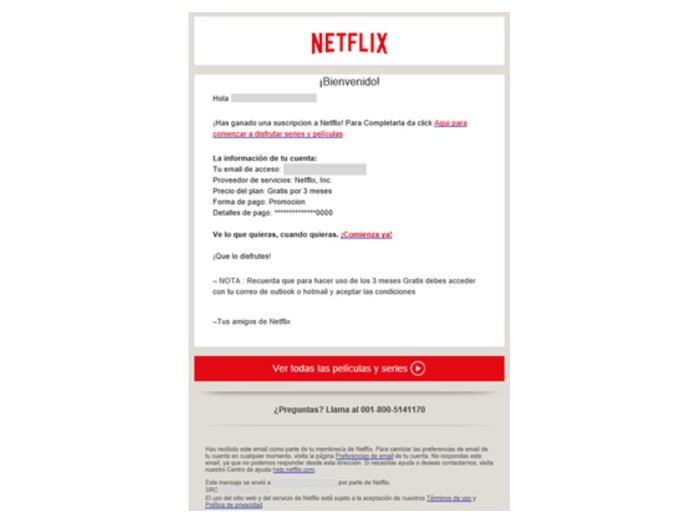 E-mail offers three months free subscription (Photo: Reproduction / Kaspersky Lab)
E-mail offers three months free subscription (Photo: Reproduction / Kaspersky Lab)
Finally, after having the user's approval, the information is sent with the privileges granted and the session token to the URL of the malicious site. Then the application will have access to all your personal data.
What makes the scam successful is the authentication process, to which many users are already accustomed. Still, the initial targeting is for the authentic site of the provider, not for a fake website like in many pishing attacks. Therefore, it becomes more difficult to identify the blow. You always have to be alert and suspicious of emails with content "too good to be true".
Không có nhận xét nào:
Đăng nhận xét